The Audit Trail Illusion: Why "Activity Logs" Are Not Compliance Tools
Just because your software "tracks changes" doesn't mean it's audit-proof. The dangerous gap between a user-friendly Activity Log and a legally defensible Audit Trail.
Every modern accounting platform, from the cheapest cloud tool to the most expensive ERP, claims to have an "Audit Trail." Sales reps love to demo it: they open an invoice, change the amount, and show you a little history tab that says "User A changed Amount from $100 to $200."
For a small business owner trying to figure out who messed up an invoice, this feature is fantastic. But for a CFO facing a tax audit, a due diligence process, or a forensic investigation, this feature is often a mirage.
The problem lies in the definition. Most SMB tools provide an Activity Log, designed for troubleshooting. Regulators require an Audit Trail, designed for non-repudiation. They are not the same thing.
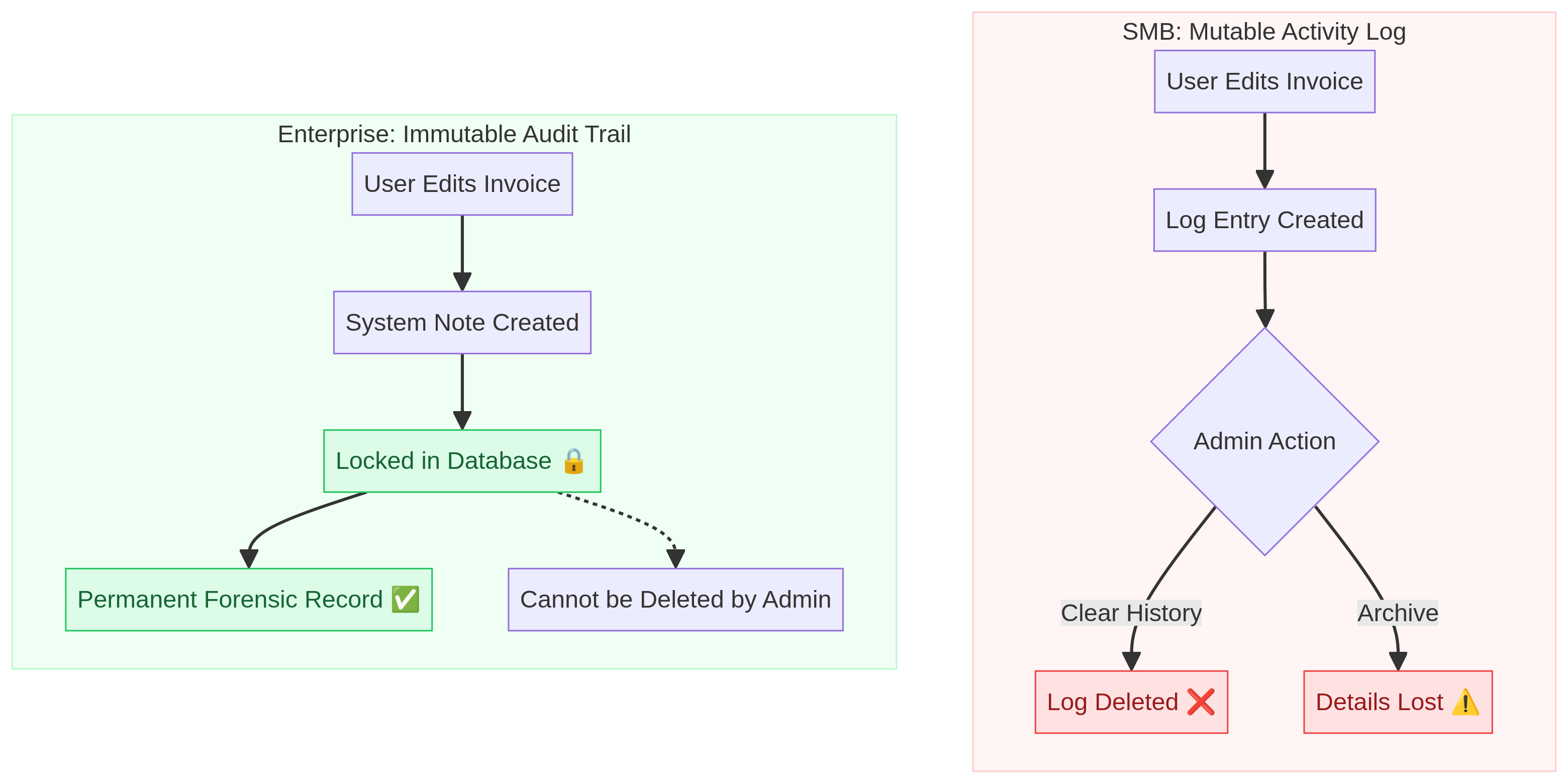
The Immutability Test
The single most important characteristic of a compliant audit trail is Immutability. Once an event is recorded, it must never be alterable or deletable by anyone—not the user, not the admin, and ideally not even the database administrator.
In many popular SMB platforms, the "Audit Log" fails this test in subtle ways:
- Purging History: Some platforms archive or "condense" data after a certain period (e.g., 7 years) to save space. When they do this, the granular transaction history—the "who, what, when"—is often flattened into a single opening balance, destroying the audit trail.
- The "Delete" Button: In some desktop-based or hybrid legacy systems, an Administrator can literally "Clear Audit Trail" to reduce file size. From a compliance perspective, this is the digital equivalent of shredding documents.
The "System Note" Standard
Enterprise systems like NetSuite use a concept called "System Notes." These are written to a separate, read-only table in the database. Even if a user has "Full Admin" rights, they cannot edit or delete a System Note. This is the standard required for SOX compliance and DCAA audits. If your software allows an Admin to "reset" or "clean up" the history, it is not an audit trail; it is a scratchpad.
The "Before and After" Gap
Another critical failure point is data granularity. A weak Activity Log might say: "User B edited Invoice #1024."
A compliant Audit Trail must say: "User B changed Field 'Unit Price' from '10.00' to '12.00' on Invoice #1024 at 14:02:33 UTC."
Without the "Before" and "After" values, the log is useless for forensic reconstruction. If you suspect fraud—for example, an employee changing a vendor's bank account number to their own and then changing it back—a log that just says "Vendor Edited" tells you nothing. You need to see what was edited.
Why This Matters for Selection
As outlined in our Enterprise Software Selection Guide, you cannot simply "add on" a compliant audit trail later. It is a core database architectural decision.
If your industry requires strict compliance (e.g., Government Contracting, Healthcare, Public Company), using software with a mutable Activity Log is a non-starter. No matter how many other features it has, if the auditor cannot trust the history, they cannot trust the books.